The blockchain security node is a crucial system component that safeguards transaction integrity and network security. The following article explains the node’s intricate role in securing the system.
What is a blockchain security node?
Blockchain security nodes act as the architects of a decentralized network’s infrastructure. Their primary responsibility is to uphold consensus on the blockchain’s public ledger, with specific tasks differing across various types of nodes.
Types of Blockchain Nodes
There are several types of blockchain nodes, each serving a specific function within the network. Some common types include:
Full Nodes
Full Nodes are integral components of a blockchain network, as they maintain a complete copy of the blockchain ledger. These nodes actively participate in the network by performing several crucial tasks:
- Storing the Blockchain: Full Nodes store the entire blockchain, including all transaction records from the Genesis block to the most recent one. This ensures redundancy and decentralization of data storage within the network.
- Validating Transactions: Full Nodes verify the validity of transactions by checking them against the consensus rules defined by the protocol. This involves confirming that transactions are correctly signed, inputs are unspent, and other criteria specified by the network’s rules.
- Relaying Transactions: Full Nodes propagate transactions across the network to other nodes once transactions are validated. This helps disseminate transaction information efficiently and ensures that all nodes have access to the latest transaction data.
- Enforcing Consensus Rules: Full Nodes play a crucial role in maintaining the integrity of the blockchain by enforcing consensus rules. These rules govern how new blocks are created, transactions are verified, and conflicts are resolved within the network.
Overall, Full Nodes are the backbone of the blockchain network, contributing to its security, decentralization, and reliability by storing, validating, and relaying transactions while upholding consensus rules.

Light Nodes (or Lightweight Nodes)
Light Nodes, also known as Lightweight Nodes, are essential components of a blockchain network, particularly for users with limited resources or bandwidth. These nodes maintain a lightweight blockchain version, typically including crucial data required for transaction verification and network participation. Here are some specific details about Light Nodes:
- Minimal Blockchain Storage: Unlike Full Nodes that store the entire blockchain, Light Nodes maintain only a subset of the blockchain data. This subset usually includes block headers, transaction headers, and other metadata necessary for verifying transactions and participating in the network.
- Transaction Verification: Light Nodes rely on Full Nodes to verify transaction validity. Instead of independently validating transactions by referencing the entire blockchain, Light Nodes sends transaction data to Full Nodes for verification. Once verified, Full Nodes sends back the confirmation to Light Nodes.
- Network Information: Light Nodes depend on Full Nodes to obtain network information, such as the latest block headers, new transaction broadcasts, and network updates. Light Nodes can stay synchronized with the blockchain network without extensive storage or computational resources.
- Reduced Bandwidth and Resource Requirements: Light Nodes are designed to operate efficiently on devices with limited resources, such as smartphones or IoT devices. By maintaining a lightweight version of the blockchain and relying on Full Nodes for transaction verification and network information, Light Nodes consume less bandwidth and computational power.
Miner Nodes
Miner nodes, often called “miners,” are specialized nodes in a blockchain network responsible for creating new blocks and validating transactions. They play a central role in networks that utilize Proof of Work (PoW) consensus mechanisms, such as Bitcoin and Ethereum (until Ethereum transitions to Proof of Stake). Here are some unique details about Miner Nodes:
- Transaction Verification and Block Creation: Miner nodes collect unconfirmed transactions, verify them, and group them into new blocks. They use computational power to solve the Proof of Work puzzle, finding a suitable nonce to create a valid new block.
- Network Security and Maintenance: Miner nodes secure the blockchain network by ensuring the integrity of transactions and preventing attacks such as the 51% attack. They maintain decentralization and network security by competing to create new blocks.
- Reward System: Miners are rewarded with newly minted cryptocurrency and transaction fees when they successfully create a new block. This reward system incentivizes them to continue maintaining and securing the network.
Pruned Full Nodes
- Definition: Pruned full nodes store only a portion of the blockchain history by discarding old data while maintaining the most recent transactions.
- Function:
- Storage Efficiency: Pruned nodes reduce storage requirements by keeping only a subset of the blockchain while still participating in transaction validation.
- Verification: They still verify all transactions and blocks from the beginning but only retain a specified amount of recent data.
Archival Full Nodes
- Definition: Archival full nodes store the complete history of the blockchain, including every transaction and block since the network’s inception.
- Function:
- Comprehensive Record: They provide the most complete blockchain record, useful for in-depth analysis and data integrity.
- Validation: These nodes validate all transactions and blocks, ensuring the accuracy and security of the blockchain.
Lightning Nodes
- Definition: Lightning nodes operate on the Lightning Network, a second-layer solution for Bitcoin and other blockchains designed to enable faster and cheaper transactions.
- Function:
- Off-Chain Transactions: Facilitate off-chain transactions that are settled on the blockchain only when necessary, reducing on-chain congestion.
- Micro-Payments: Support micro-payments and high-frequency transactions efficiently.
Masternodes
- Definition: Masternodes are specialized nodes in certain blockchain networks (like Dash) that perform additional functions beyond regular transaction validation.
- Function:
- Governance: Participate in voting on network proposals and decisions.
- Enhanced Services: Provide services like transaction mixing for privacy, instant transactions, and more robust network security.
- Incentives: Typically require a significant stake in the network’s cryptocurrency, earning rewards for their additional responsibilities.
Authority Nodes
- Definition: Authority nodes are used in permissioned blockchain networks where participants are known and trusted entities, such as in Proof of Authority (PoA) systems.
- Function:
- Block Validation: Validate transactions and create new blocks based on their established authority.
- Network Governance: Often have governance responsibilities, making network rules and operations decisions.
Super Nodes
- Definition: Supernodes are enhanced nodes critical to maintaining the network’s infrastructure. They are often found in more centralized blockchain models or specific projects like NEO.
- Function:
- Network Stability: Ensure the network remains stable and operational.
- Additional Services: May offer transaction processing, governance functions, and network maintenance services.
Staking Nodes
- Definition: Staking nodes, used in Proof of Stake (PoS) networks, participate in the block creation by holding and “staking” a significant amount of cryptocurrency.
- Function:
- Block Validation: Validate and propose new blocks based on the cryptocurrency they hold and stake in the network.
- Incentives: Earn rewards proportional to their stake for maintaining the network’s security and consensus.
Role of blockchain security node
Blockchain nodes play a critical role in ensuring the security of a blockchain network. Here’s how:
Consensus Mechanism: Nodes participate in the blockchain’s consensus mechanism, which is the process by which agreement is reached on the validity of transactions and the addition of new blocks to the chain. This agreement ensures that only valid transactions are added to the blockchain, maintaining its integrity and security.
Transaction Validation: Nodes validate transactions by verifying their cryptographic signatures and ensuring that they adhere to the rules of the blockchain protocol. This process helps prevent fraudulent or malicious transactions from being included in the blockchain, enhancing security.
Decentralization: The distributed nature of blockchain nodes contributes to the network’s decentralization. Decentralization makes it more difficult for malicious actors to compromise the network, as they would need to control a significant portion of the nodes to carry out attacks successfully.
Data Storage and Replication: Nodes store copies of the blockchain ledger, ensuring redundancy and resilience against data loss or tampering. This data replication across multiple nodes makes it challenging for attackers to alter the blockchain’s history, thus enhancing its security.
Network Security: Nodes actively participate in securing the network by relaying transactions, propagating blocks, and maintaining peer-to-peer connections. This collective effort helps prevent network attacks and ensures the smooth operation of the blockchain.
Consensus Enforcement: Nodes enforce the consensus rules of the blockchain protocol, which govern how consensus is achieved and maintained. By adhering to these rules, nodes prevent malicious actors from attempting to manipulate the consensus process, thereby preserving the network’s security.

Threats to Blockchain Security Node
Several threats pose risks to the security of blockchain nodes. Some of the prominent ones include:
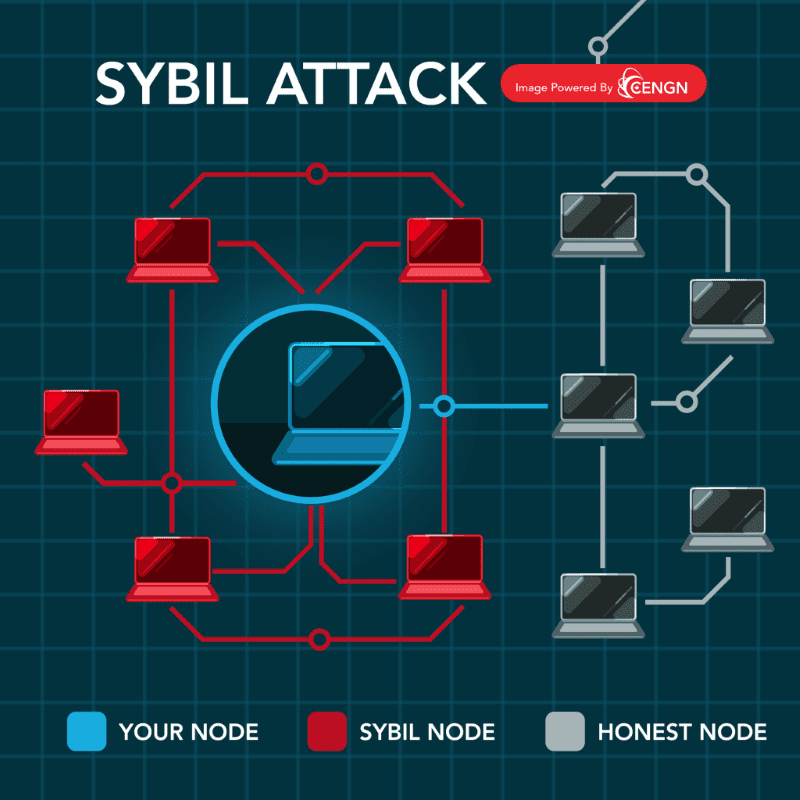
Sybil Attacks
In a Sybil attack, the attacker exploits the decentralized nature of the blockchain network by creating numerous fake identities or nodes under their control. These Sybil nodes can be distributed across the network and may appear as legitimate participants to other nodes. By controlling a significant portion of the network’s nodes, the attacker gains disproportionate influence and can manipulate the consensus process or disrupt the regular operation of the network.
The attacker can use Sybil nodes to carry out various malicious activities, including:
- Double Spending: By controlling multiple nodes, the attacker can attempt to spend the same cryptocurrency units more than once. They can broadcast conflicting transactions to different parts of the network, leading to confusion and potentially allowing them to spend funds they don’t own.
- Denial of Service (DoS) Attacks: Sybil nodes can flood the network with invalid transactions or data, overwhelming legitimate nodes and disrupting their ability to process transactions or reach consensus. This can result in network congestion, delays, or even temporary shutdowns.
- Manipulation of Consensus: With a significant number of Sybil nodes under their control, the attacker can influence the consensus mechanism of the blockchain network. They may attempt to dictate which transactions are included in the next block or even try to rewrite the blockchain’s history, leading to a fork in the blockchain.
- Economic Attacks: Sybil’s attacks can have financial implications besides directly manipulating transactions or consensus. For example, the attacker may use their control over multiple nodes to manipulate market prices or disrupt the regular operation of decentralized applications (dApps) built on the blockchain.
DDoS Attacks
In a Distributed Denial of Service (DDoS) attack, the attacker attempts to disrupt the regular operation of a blockchain node by flooding it with a massive volume of malicious traffic. This flood of traffic overwhelms the node’s resources, such as bandwidth, processing power, or memory, making it unable to respond to legitimate requests effectively.
DDoS attacks typically involve multiple compromised computers or devices, known as botnets, which the attacker controls remotely. These botnets are often spread across various locations and networks, making mitigating the attack by simply blocking a single traffic source challenging.
Once the targeted blockchain node becomes inundated with traffic from the DDoS attack, it may experience several adverse effects, including:
- Network Congestion: The flood of malicious traffic congests the blockchain node’s network connection, making it difficult for legitimate transactions and data to reach the node. This can lead to delays in transaction processing and block propagation, affecting the overall performance of the blockchain network.
- Resource Exhaustion: The excessive volume of incoming requests consumes the node’s resources, such as CPU usage, memory, or disk space. As a result, the node may become unresponsive or crash, rendering it unable to participate in the network and process transactions.
- Availability Issues: DDoS attacks can cause prolonged downtime for the targeted blockchain node, preventing it from fulfilling its role in maintaining the network’s security and consensus. This disruption in availability undermines the reliability and trustworthiness of the blockchain network, potentially leading to financial losses or reputational damage.

Software vulnerabilities
Software vulnerabilities refer to weaknesses or flaws in software applications or systems that attackers can exploit to compromise the software’s security, integrity, or availability. These vulnerabilities can exist in various software stack components, including the operating system, libraries, frameworks, and application code. Here are some common types of software vulnerabilities:
- Buffer Overflow: Buffer overflow occurs when a program writes data beyond the bounds of an allocated memory buffer, leading to the corruption of adjacent memory locations. Attackers can exploit buffer overflow vulnerabilities to execute arbitrary code or trigger a denial-of-service (DoS) condition.
- SQL Injection: SQL injection occurs when an attacker inserts malicious SQL code into input fields of a web application, exploiting vulnerabilities in the application’s database layer. This can allow attackers to execute unauthorized database queries, retrieve sensitive information, or modify database records.
- Cross-Site Scripting (XSS): Cross-Site Scripting occurs when an attacker injects malicious scripts into web pages viewed by other users. These scripts can execute in the context of the victim’s browser, allowing attackers to steal session cookies, redirect users to malicious websites, or perform other malicious actions.
- Cross-Site Request Forgery (CSRF): CSRF occurs when an attacker tricks a user into performing unintended actions on a web application where the user is authenticated. This can lead to unauthorized transactions, data manipulation, or account takeover.
- Authentication Bypass: Authentication bypass vulnerabilities allow attackers to gain unauthorized access to protected resources or functionalities without providing valid credentials. This can occur due to flaws in authentication mechanisms, session management, or access control logic.
- Privilege Escalation: Privilege escalation vulnerabilities allow attackers to gain elevated privileges or access levels beyond their intended permissions. This can occur due to weaknesses in access control mechanisms, configuration settings, or software design flaws.
- Remote Code Execution (RCE): Vulnerabilities allow attackers to execute arbitrary code remotely on a target system or application. This can result in complete system compromise, unauthorized data access, or further exploitation of the underlying infrastructure.
Mitigating software vulnerabilities requires proactive measures such as regular software updates, code reviews, vulnerability assessments, penetration testing, and implementing security best practices throughout the software development lifecycle. Additionally, organizations should stay informed about emerging threats and vulnerabilities and promptly apply patches or mitigations to address known security issues.
Solution for blockchain security node
Securing blockchain nodes is crucial for maintaining the integrity and reliability of the entire blockchain network.
Implementing robust security solutions like firewalls safeguards blockchain nodes from potential threats and unauthorized access.
Use a firewall
A firewall solution is instrumental in fortifying the security of blockchain nodes by erecting a protective barrier against unauthorized access attempts. Firewalls effectively thwart malicious actors from infiltrating blockchain nodes by meticulously defining access policies and filtering network traffic. This proactive measure ensures the sanctity of the blockchain network, bolstering its resilience against potential cyber threats and unauthorized breaches.
Update software regularly
Regular software updates are critical to a comprehensive security strategy for blockchain nodes. Organizations can promptly apply patches and updates to address known security vulnerabilities within blockchain node software. This proactive approach minimizes the risk of exploitation by malicious actors seeking to exploit software flaws. Additionally, staying vigilant for security advisories and promptly addressing identified security issues ensures blockchain nodes’ continued integrity and security.
Use strong passwords
Strong passwords are fundamental to securing blockchain nodes against unauthorized access. By implementing robust password policies, such as requiring complex combinations of characters, numbers, and symbols, organizations can enhance the resilience of their blockchain nodes to potential attacks. Strong passwords act as a first line of defense, thwarting brute-force attacks and unauthorized intrusion attempts. Furthermore, enforcing regular password updates and employing multi-factor authentication mechanisms further fortify the security posture of blockchain nodes, safeguarding sensitive blockchain data from unauthorized access and potential compromise.
Data backup
Implementing a robust data backup solution is essential for securing blockchain nodes and mitigating the risk of data loss in a node compromise. By regularly backing up blockchain data to secure and off-site locations, organizations can ensure the availability and integrity of critical blockchain data, even in the face of cyber-attacks or node failures.
A comprehensive data backup strategy involves:
- Regular Backups: Establishing a schedule for regular backups of blockchain data ensures that recent and accurate copies of the blockchain ledger are readily available for recovery purposes.
- Off-site Storage: Storing backup copies of blockchain data in off-site locations, such as cloud storage or remote servers, provides an additional layer of protection against physical damage, theft, or localized disasters that may affect the primary node environment.
- Encryption: Encrypting backup data helps protect sensitive blockchain information from unauthorized access during storage or transmission, ensuring confidentiality and compliance with data security regulations.
- Versioning: Implementing versioning mechanisms allows organizations to maintain multiple backup copies of blockchain data over time, enabling them to roll back to previous states in case of data corruption or unauthorized modifications.
- Testing and Validation: Regularly testing backup procedures and validating backup integrity ensures that backup copies of blockchain data are reliable and can be restored when needed.

Why do I need a blockchain node provider?
A blockchain node provider offers several benefits that make it valuable for various use cases. Here are some reasons why you might need a blockchain node provider:
Access to Blockchain Networks: Blockchain node providers offer access to various blockchain networks, allowing developers and businesses to interact with the blockchain without running their nodes. This is particularly beneficial for those who want to leverage blockchain technology without the resources or technical expertise to maintain a node infrastructure.
Infrastructure Management: Running a blockchain node requires significant resources, including hardware, bandwidth, and maintenance efforts. Blockchain node providers manage infrastructure, ensuring that nodes are always available, up-to-date, and properly configured. This frees up resources and time for developers and businesses to focus on their core activities.
Reliability and Uptime: Blockchain node providers typically operate large-scale node infrastructure with redundant systems and high availability. This ensures reliable access to blockchain networks, minimizing downtime and disruptions. Relying on a node provider can be crucial for businesses and applications that require continuous access to blockchain data and services.
Scalability: Blockchain node providers offer scalable solutions that accommodate growing demand and workload requirements. As blockchain networks expand and evolve, node providers can dynamically allocate resources to meet demand spikes and scale infrastructure accordingly. This scalability is essential for applications with fluctuating usage patterns or rapidly growing user bases.
Developer Tools and APIs: Many blockchain node providers offer developer tools, APIs, and SDKs that streamline blockchain integration and development. These tools provide easy access to blockchain data, functionalities, and services, simplifying development and reducing time-to-market for blockchain-based applications.
Cost Savings: Setting up and maintaining a blockchain node infrastructure can be costly, especially for small businesses and startups. Blockchain node providers offer cost-effective solutions with pay-as-you-go pricing models, allowing companies to pay only for the resources they use. This cost savings can make blockchain technology more accessible and affordable for a broader range of applications and use cases.
Overall, blockchain node providers play a vital role in democratizing access to blockchain networks, simplifying blockchain development and integration, and enabling businesses to harness the benefits of blockchain technology without the complexities and overhead of managing their node infrastructure.

In today’s digital landscape, the keyword “blockchain security node” is crucial in safeguarding blockchain systems against network threats. These nodes ensure the secure and transparent operation of the blockchain and represent significant strides in building a trustworthy digital platform. By guaranteeing security, transparency, and decentralization, blockchain security nodes are pillars for future blockchain systems’ development and stability.
Accessing a Proxy Rotating website can provide further detailed information on blockchain security nodes and their functions.
>>> See more:
Blockchain security statistics
Blockchain security vs cyber security
Blockchain security transaction system project
