Decentralized VPN DPN is an emerging concept in the field of network security. Instead of relying on a central server, these systems utilize a distributed network of devices to provide VPN and private network services. This creates a more secure environment and protects user privacy while reducing the risk from centralized points vulnerable to attacks. Additionally, it offers greater flexibility and anonymity for users when accessing the Internet.
What is a DPN VPN
A decentralized private network (DPN) operates without a central authority or server, using a distributed network of nodes to route internet traffic securely. It enhances privacy by dispersing data across multiple devices, reducing the risk of single-point vulnerabilities. This approach provides users with increased anonymity and protection against surveillance or censorship.

How does a decentralized VPN work?
A decentralized VPN (dVPN) works by routing your internet traffic through a distributed network of independent nodes instead of centralized servers controlled by a single provider. Here’s how it works:
- Decentralized Architecture: Unlike traditional VPNs, dVPNs operate on a peer-to-peer network model with no central control. Users can volunteer their devices as nodes to help route and secure traffic.
- Encryption and Routing: When you connect to a dVPN, your internet traffic is encrypted and routed through multiple nodes in the distributed network. This enhances privacy by making it difficult to trace your activities back to you.
- Blockchain Technology: Decentralized VPNs often utilize blockchain and distributed ledger technologies to manage the network securely and transparently. Smart contracts automatically enforce network rules and transactions without a central authority.
- Compensation for Node Operators: Users who volunteer their devices as nodes can earn cryptocurrency or special tokens for helping route traffic and selling unused bandwidth. This incentivizes participation in the network.
- Transparency and Accountability: Since no single entity controls the network, dVPNs aim to provide more transparency than traditional VPNs. However, there are also challenges around accountability and legal compliance since different nodes may have varying standards.
In summary, decentralized VPNs leverage a distributed network of nodes, encryption, and blockchain technology to provide an alternative to centralized VPN services, to enhance privacy, security, and transparency
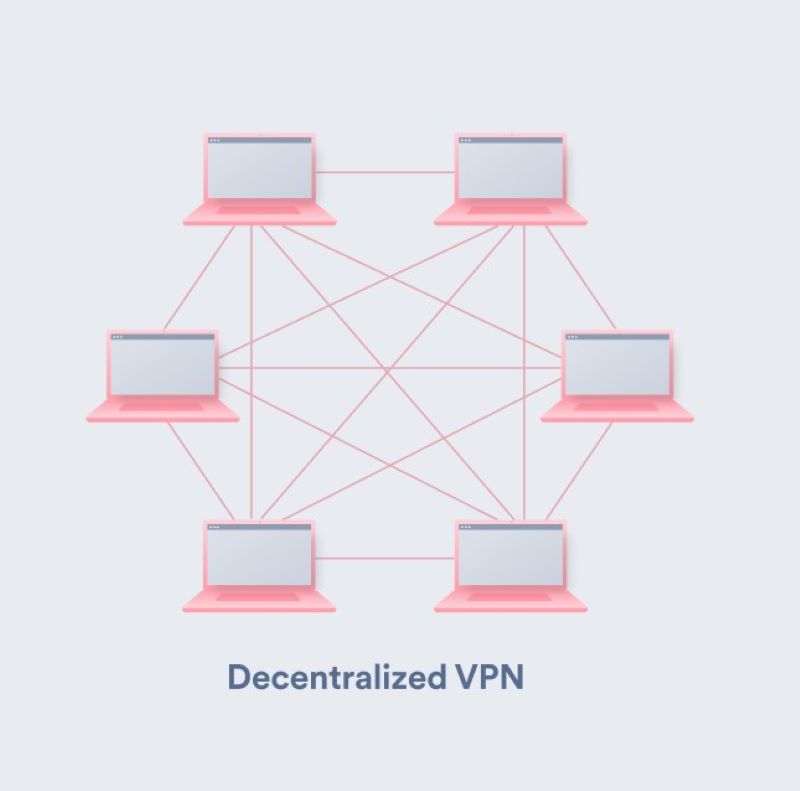
Advantages of Decentralized Private Network DPN
Decentralized VPNs provide multiple benefits compared to traditional VPNs:
- Enhanced Privacy: Decentralized VPNs offer heightened privacy by encrypting users’ online traffic and mixing it with others, making it challenging for third parties to trace individual activities. Moreover, these VPNs avoid storing logs or user data, safeguarding privacy.
- Security: Data encryption and the distributed network architecture of decentralized VPNs significantly reduce the risk of centralized data breaches and cyberattacks. By dispersing network functionality across multiple nodes, these VPNs enhance overall security for users.
- Resistance to Censorship: With no central server to target, decentralized VPNs are challenging for authorities to censor or block. This resistance to censorship mitigates the risk of data logging and surveillance, providing users with greater freedom and privacy online.
- Resistance to Shutdown: Due to their distributed nature, decentralized VPNs are inherently difficult for authorities to shut down or regulate. This resilience makes them particularly suitable for users in regions with restricted internet access, ensuring continuous and unrestricted connectivity.
- User Incentives: Users of decentralized VPNs are often incentivized to operate nodes within the network. This incentivization fosters community participation and strengthens the network, enhancing its resilience and reliability for all users.

Disadvantages of Decentralized VPN DPN
While Decentralized Private Network DPN offers numerous advantages, they also come with certain disadvantages:
- Slower Speeds: Routing through multiple nodes may make connection speeds slower than centralized VPNs.
- Security Risks: The decentralized nature and volunteer-based model mean trusting unknown node operators, posing potential security risks.
- Complexity: Decentralized private network DPN is complex to set up and use, catering primarily to tech-savvy users. Non-technical users may need help navigating.
- Limited User Base and Support: A more minor user base results in fewer available nodes and slower performance. Additionally, customer support may be limited due to these networks’ decentralized nature.
- Regulatory Ambiguity: The legal status of decentralized VPNs can be unclear or vary by region, potentially putting users at risk of unknowingly violating local laws.

Solutions of Decentralized Private Network DPN
In an era of growing digital privacy and security concerns, decentralized VPN DPN solutions have emerged as innovative approaches to address these challenges. Two notable examples include Deeper Connect Pico & Nano and Surfshark Decentralized VPN.
Deeper Connect Pico & Nano
Deeper Connect Pico & Nano represent pioneering solutions in decentralized VPNs. These compact devices utilize blockchain technology to establish decentralized private networks, offering users enhanced privacy and security. Key features include:
Decentralized Infrastructure: Deeper Connect Pico & Nano operates on a distributed network architecture, eliminating reliance on centralized servers and reducing vulnerabilities.
Advanced Encryption: These devices utilize robust encryption protocols to encrypt users’ internet traffic, ensuring confidentiality and data integrity.
Privacy Enhancements: Deeper Connect Pico & Nano enhances user privacy by mixing and routing traffic through multiple nodes, making it difficult for third parties to track online activities.
Ease of Use: With user-friendly interfaces and plug-and-play functionality, these devices offer seamless integration into users’ existing networks, catering to novice and experienced users.
Surfshark Decentralized VPN
Surfshark Decentralized VPN is another notable player in dVPN solutions, offering users a decentralized alternative to traditional VPN services. Key highlights of Surfshark Decentralized VPN include:
Global Network: Surfshark’s decentralized VPN network spans numerous nodes worldwide, providing users with widespread coverage and optimal performance.
Zero-Knowledge Architecture: Surfshark operates on a zero-knowledge architecture, meaning it does not store user logs or personal information, ensuring maximum privacy and anonymity.
Unrestricted Access: By bypassing geo-restrictions and censorship measures, Surfshark Decentralized VPN enables users to access content and websites without limitations, regardless of location.
Advanced Security Features: Surfshark employs cutting-edge encryption protocols and security measures to safeguard users’ data and protect against cyber threats, ensuring a secure online experience.

How to set up and use Decentralized VPN DPN
Setting up and using a Decentralized VPN (dVPN) typically involves the following steps:
Step 1: Choose a dVPN Provider
Research and select a decentralized VPN provider that meets your privacy and security needs. Some popular dVPN providers include Deeper Connect, Mysterium Network, and Tachyon Protocol.
Step 2: Sign Up and Create an Account
Visit the website of your chosen dVPN provider and sign up for an account. Complete the registration process and submit the information to set up your account.
Step 3: Download and Install the Software
After creating your account, download the dVPN software or app the provider provides. Install the software on your device, ensuring compatibility with your operating system (Windows, macOS, Linux, Android, iOS, etc.).
Step 4: Configure Settings
Open the dVPN software or app and configure the settings according to your preferences. This may include selecting your desired server locations, enabling or disabling certain features (such as kill switch or split tunneling), and adjusting encryption settings.
Step 5: Connect to the Network
Once the settings are configured, you can connect to the decentralized VPN network by selecting a server location and clicking the “Connect” button within the software or app.
Step 6: Verify Connection
After connecting to the dVPN network, verify that your internet traffic is being routed through the decentralized network. You can do this by checking your IP address using online tools or visiting websites that display your IP address.
Step 7: Browse Securely
With the dVPN connection established, you can now browse the Internet securely and anonymously. Your online activities are encrypted and routed through multiple nodes, enhancing privacy and security.
Step 8: Disconnect and Exit
When you’re finished using the dVPN, remember to disconnect from the network by clicking on the “Disconnect” button within the software or app. You can exit the dVPN software to ensure it’s not running in the background.
Step 9: Update Software Regularly
Install any available updates to keep your dVPN software or app up to date. This ensures that you receive the most recent security updates and features.
The future of Decentralized VPN DPN
The future of Decentralized VPN (dVPN) is characterized by a convergence of technological innovation, rising concerns over digital privacy, and evolving regulatory landscapes. As the Internet becomes more intertwined with our daily lives and the volume of sensitive data transmitted online continues to grow, the demand for secure and private Internet connections is skyrocketing. In response to this demand, decentralized VPN DPN solutions are poised to play a pivotal role in reshaping the landscape of online privacy and security.
One of the primary drivers of the future growth of decentralized VPN DPN is the continuous advancement of blockchain and cryptographic technologies. These technologies underpin the decentralized architecture of decentralized VPN DPN platforms, enabling the creation of secure and censorship-resistant networks. By leveraging blockchain’s immutable ledger and cryptographic techniques such as encryption and hashing, decentralized VPN DPN providers can ensure that users’ online activities are shielded from prying eyes and malicious actors.
Furthermore, integrating decentralized VPN DPN solutions with emerging Web 3.0 technologies is expected to unlock new possibilities and use cases. Web 3.0 emphasizes principles of decentralization, interoperability, and user sovereignty, aligning closely with the ethos of decentralized VPN DPN platforms. By integrating with other Web 3.0 technologies, such as decentralized identity and finance, decentralized VPN DPN solutions can offer users greater control over their online identities and financial transactions, further enhancing their utility and appeal.

How do you choose a reliable VPN that fits your needs?
Here are the key factors to consider when choosing a reliable VPN for your needs:
Security and Privacy
- Look for a VPN with strong encryption like AES-256, which is virtually unbreakable
- Ensure the VPN has a strict no-logs policy and is based in a privacy-friendly jurisdiction
- Prioritize VPNs that have been independently audited to verify their security claims
Speed and Performance
- Choose a VPN with an extensive network of high-speed servers to ensure good performance
- Test the VPN’s speeds on servers in locations where you need to access content from
- Avoid free VPNs, which often have slower speeds and bandwidth caps
Ease of Use
- Pick a VPN with user-friendly apps for all your devices and platforms
- Look for features like automatic connection, split-tunneling, and a kill switch
- Ensure the VPN is easy to set up and configure on your router if needed
Additional Features
- Consider extra features like ad-blocking, malware protection, and multi-hop connections
- Look for a VPN that allows torrenting and P2P traffic if that’s important to you
- Ensure the VPN has a large number of simultaneous connections allowed
Reputation and Transparency
- Choose a VPN provider with a proven track record and positive reviews
- Prioritize VPNs that are transparent about their company, leadership, and jurisdiction
- Avoid free VPNs and lesser-known providers, as they may have hidden issues
Considering these factors, you can find a reliable VPN that meets your security, privacy, performance, and features needs. Paid VPNs from reputable providers are generally a safer bet than free options
In the ever-growing landscape of online privacy and security concerns, the development of decentralized VPN DPN solutions has emerged as a significant trend. This is crucial in safeguarding users’ personal information from increasingly sophisticated online threats. Decentralized VPNs provide a secure and private means of accessing the Internet and enhance online freedom and anonymity. However, it is essential to consider the challenges and limitations in deploying and utilizing this technology, including performance, network resources, and the reliability of network nodes. In summary, despite the obstacles, the advancement of Decentralized private network DPN solutions signifies a significant step forward in protecting users’ online privacy and security worldwide. Please visit the Proxy Rotating website for more details and updated helpful information.
>>> See more:
Deeper connect mini decentralized vpn firewall hardware
