Layer 3, the Network Layer in the OSI model, is crucial in routing data across networks. To gain a deeper understanding of the structure and operations of Layer 3 VPN Protocols, this article by Proxy Rotating will delve into the details of this network layer. Dive in to grasp and apply the essential knowledge in practical networking scenarios!
What do MPLS Layer 3 VPN protocols mean?
Layer 3 VPN (L3VPN) operates at the OSI model’s network layer, responsible for IP-based routing and packet forwarding. Enterprises and service providers widely use L3VPN to provide a secure and scalable way to connect multiple sites over a shared infrastructure, such as the public Internet or a private network.
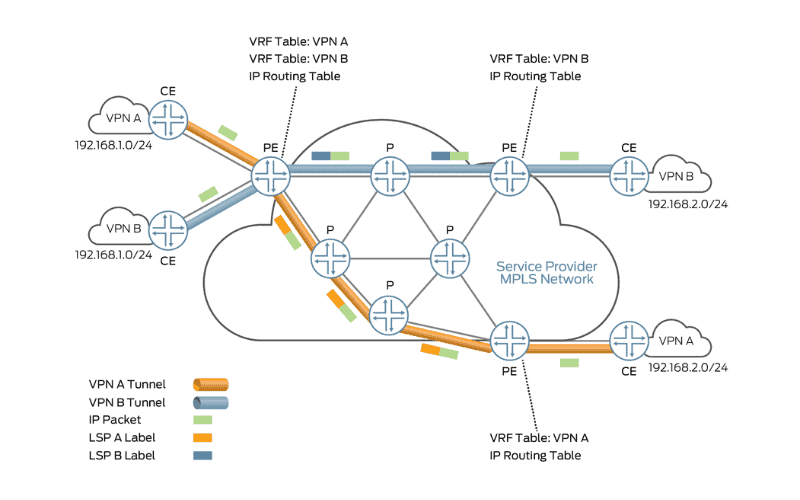
How MPLS L3VPN works
MPLS L3VPN (Multiprotocol Label Switching Layer 3 Virtual Private Network) is a technology that connects geographically dispersed VPN sites using BGP (Border Gateway Protocol) to advertise VPN routes and MPLS (Multiprotocol Label Switching) to forward VPN packets over a service provider backbone. Here is an overview of how MPLS L3VPN operates:
Basic Architecture:
- Customer Edge (CE) Device: This device resides on the customer network and is directly connected to the service provider network but does not support MPLS.
- Provider Edge (PE) Device: Located at the edge of the service provider network, connected to CEs, and processes all MPLS VPN services.
- Provider (P) Device: The core device on the service provider network, with essential MPLS forwarding capability, does not handle VPN routing information.
Networking Schemes:
- Route Target Attributes: Control the advertisement and reception of VPN routes between sites, allowing for flexible VPN access control and various networking schemes.
- Basic VPN Networking Scheme: Involves assigning a unique route target to each VPN to segregate traffic, ensuring users within a VPN can communicate but are isolated from users in other VPNs.
Packet Forwarding:
- Outer Tag: This tag identifies the public tunnel from the local PE to the remote PE, enabling VPN packet forwarding along the public tunnel.
- Inner Label: Identifies the remote VPN site, facilitating packet forwarding within the VPN.
Route Advertisement:
- Local CE to Ingress PE: CE advertises standard IPv4 routing information to the ingress PE.
- Ingress PE to Egress PE: Ingress PE adds RDs and route target attributes to standard IPv4 routes, creating VPN-IPv4 routes and advertises them to the egress PE through MP-BGP.
- Egress PE to Remote CE: Egress PE compares route attributes and advertises routes to the connected CE.
Configuration:
- MPLS L3VPN FRR (Fast Reroute): Provides backup following hop options for BGP routes in the VPN instance, ensuring network resilience in case of link failures.
MPLS L3VPN offers a robust and scalable solution for interconnecting VPN sites securely and efficiently, making it a widely used technology in modern networking environments.

MPLS L3VPN major components
The significant components of MPLS L3VPN are:
- Customer Edge (CE) Device: This device resides on the customer network and is directly connected to the service provider network but does not support MPLS.
- Provider Edge (PE) Device: Located at the edge of the service provider network, connected to CEs, and processes all MPLS VPN services.
- Provider (P) Device: The core device on the service provider network, with essential MPLS forwarding capability, does not handle VPN routing information.
- VPN Routing and Forwarding (VRF) Table: This table allows for separate and private VPN forwarding decisions to coexist within a PE device. A VRF is created per VPN within each PE.
- Route Target Attributes: Used to control the advertisement and reception of VPN routes between sites, allowing for flexible VPN access control and various networking schemes.
- MPLS Label: Consists of an outer tag that identifies the public tunnel from the local PE to the remote PE and an inner label that identifies the remote VPN site.
- MP-BGP: Used to advertise VPN-IPv4 routes among PEs.
These components work together to enable MPLS L3VPN functionality, providing secure and efficient interconnection of geographically dispersed VPN sites over a service provider’s MPLS network.
Distinguish between MPLS Layer 3 VPN protocols and Layer 2 VPN protocols
| Characteristics | Layer 3 VPN (L3VPN) Protocols | Layer 2 VPN (L2VPN) Protocols |
| Operation layer | It operates at the network layer of the OSI model and involves IP-based routing. | Functions at the data link layer of the OSI model, which handles data framing. |
| Functionally | Manages the routing of IP packets between different sites using IP routing protocols. It encapsulates entire IP packets, including the payload and the header, allowing for end-to-end IP connectivity. | It connects different sites by extending a broadcast domain or LAN segment. It encapsulates Layer 2 frames, such as Ethernet frames, allowing for a transparent bridge between networks that appear on the same LAN. |
| Common Protocols | Includes MPLS VPN, which uses label switching, and IPsec, which secures IP communications by authenticating and encrypting each IP packet. | This includes Pseudodowire Emulation (PWE) and Virtual Private LAN Service (VPLS), which extend Layer 2 services over MPLS networks. |
| Routing awareness | Capable of understanding and manipulating IP routing information, which allows it to support complex network topologies and routing policies. | It operates below the IP layer and cannot manage IP routes. It provides point-to-point or multipoint Layer 2 connectivity across a Layer 3 network. |
| Use cases | Typically used by enterprises and service providers to extend network services over a shared infrastructure, ideal for site-to-site connectivity. | This is useful for data centers and providers needing to deliver Layer 2 data link layer services over a geographically dispersed network. |
The main difference lies in the OSI model layer they operate on and how they handle traffic. Layer 3 VPNs are more about routing and connectivity across networks with IP routing, suitable for complete network connections between sites. In contrast, Layer 2 VPNs focus on extending the data link layer connectivity, which is ideal for services that require transparency in LAN services across different locations.
Benefits of MPLS Layer 3 VPN protocols
Layer 3 VPN protocols provide several significant benefits, particularly in terms of network management, scalability, and security:
Enhanced security
- Traffic isolation: Each VPN customer’s traffic is isolated within the service provider’s network, ensuring that data remains private and secure from other users on the same network.
- Encryption: Protocols like IPsec used in Layer 3 VPNs encrypt the data transmitted over the network, protecting sensitive information from potential interception and unauthorized access.
Scalability
- Efficient use of resources: Layer 3 VPNs can handle thousands of routes within the VPN, allowing them to scale efficiently as more sites are added.
- Flexible connectivity options: Businesses can easily add new sites or remote users to their network, adapting to changes in size and scope without extensive infrastructure changes.
Improved performance
- Optimized routing: Layer 3 VPNs make intelligent routing decisions based on IP headers, allowing traffic to be dynamically routed through the most efficient paths.
- Quality of service (QoS): Supports QoS for managing bandwidth and handling different types of traffic, ensuring that critical applications receive the necessary bandwidth and performance.
Network simplification
- Routing transparency: Customers can control their routing protocols, simplifying network management and integration into existing corporate networks.
- Centralized management: Businesses can centrally manage their network’s routing policies, even though the physical network infrastructure is outsourced to the VPN provider.
Global accessibility
- Worldwide network access: Layer 3 VPNs facilitate easy connection of geographically dispersed sites, allowing global enterprises to maintain a unified network presence and ensuring all branches can access central resources.
These advantages make Layer 3 VPN protocols a robust solution for enterprises looking to extend their network securely and efficiently across multiple locations.
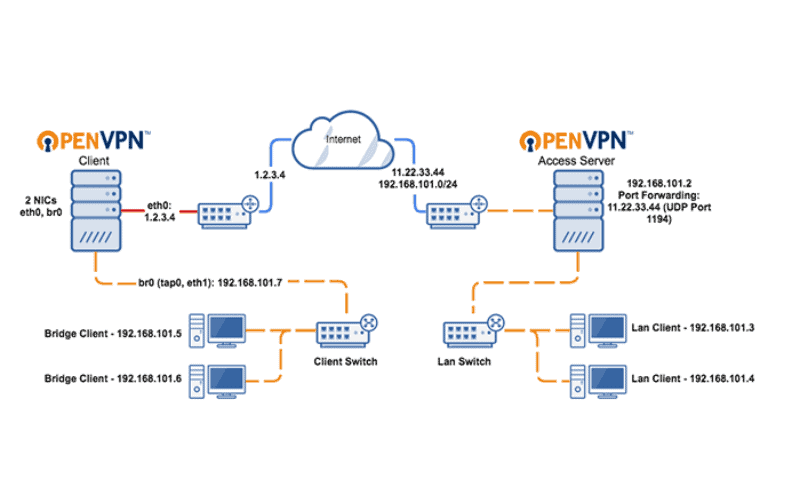
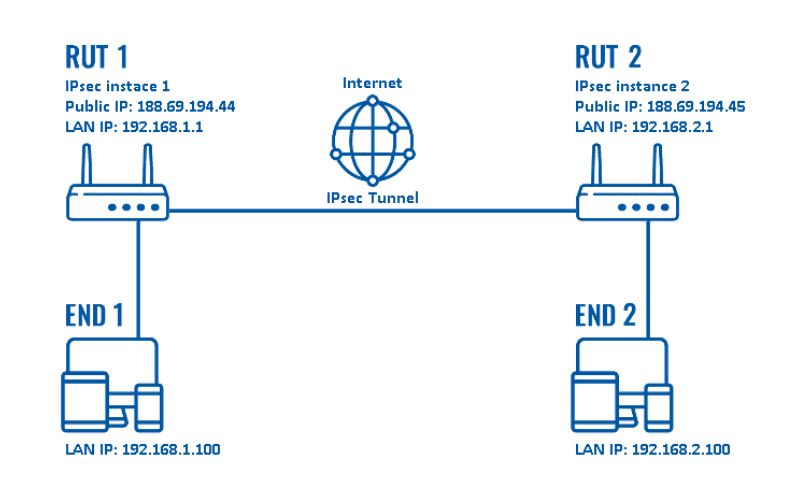
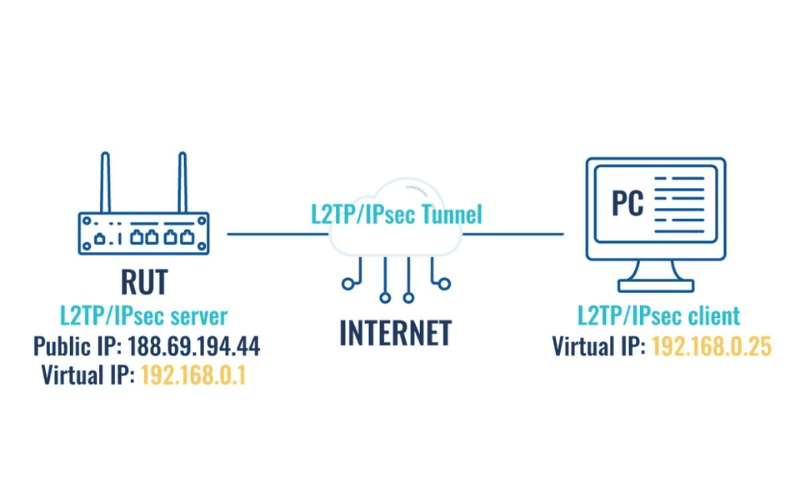
Popular types of MPLS Layer 3 VPN protocols
Here’s an overview of some popular types of Layer 3 VPN protocols, each designed to address specific security, performance, and deployment needs in varied network environments:
IPSec (Internet Protocol Security)
- Purpose: IPSec is primarily used to secure Internet communications and can operate in two modes: Transport and Tunneling. It provides a high level of security by encrypting the entire IP packet for tunnel mode or only the payload for transport mode.
- Features: Includes robust encryption, authentication, and integrity checks. It’s widely used for establishing secure connections over the Internet.
OpenVPN
- Purpose: OpenVPN is an open-source VPN protocol known for its flexibility and robust security. It can traverse network address translators (NATs) and firewalls.
- Features: Supports a variety of cryptographic algorithms, is highly configurable, and works on multiple platforms, making it a popular choice for personal VPNs and enterprise networks.
L2TP/IPsec
- Purpose: Layer 2 Tunneling Protocol (L2TP) combined with IPSec is a popular choice for deploying secure VPN communications over the Internet. L2TP does not provide encryption or confidentiality, so it is usually paired with IPSec.
- Features: While L2TP forms the tunnel, IPSec handles encryption, channel security, and data integrity checks to secure the communications.
IKEv2 (Internet Key Exchange version 2)
- Purpose: IKEv2 sets up a security association in the IPsec protocol suite. It is known for its stability and ability to re-establish a VPN connection when users temporarily lose their Internet connection.
- Features: IKEv2 provides strong security, supports automatic negotiation of security parameters, and is highly efficient in managing keys. It is particularly well-suited for use with mobile devices.
BGP (Border Gateway Protocol)
- Purpose: While not a VPN protocol in the traditional sense, BGP is often used in large-scale VPN implementations, especially in MPLS networks used by service providers. It does not encrypt data but manages routing information between different hosts on the Internet, making it crucial for operating a Layer 3 VPN.
- Features: BGP allows the creation of scalable and dynamic internetworks by managing data packets’ routes or paths.
These LInternetPN protocols are tailored to fit different network requirements, providing everything from basic tunneling and encryption to complex routing capabilities across expansive networks. Each has strengths, making them suitable for various network deployments, from individual user VPNs to enterprise-grade solutions.
Choose the suitable MPLS Layer 3 VPN protocols.
Choosing the proper Layer 3 VPN protocol involves balancing security, performance, and compatibility needs specific to your network environment. Here’s a concise guide to help you select the most suitable Layer 3 VPN protocol:
Security needs
High Security: Choose IPSec or OpenVPN for the best encryption and authentication, ideal for sensitive data protection.
Efficient Security with Speed: IKEv2 offers robust security with the ability to quickly re-establish dropped connections, making it excellent for mobile users.
Network configuration and scalability
Large Enterprises: BGP/MPLS VPNs are suitable for complex, large-scale networks due to their scalability and efficient handling of high traffic volumes.
Simpler Setups: L2TP/IPsec provides good security, is easy to set up, and is widely supported by various devices and operating systems.
Performance requirements
Customizable Performance: OpenVPN is highly configurable and can be optimized for specific network conditions.
Mobile and Dynamic Networks: IKEv2 works well in mobile scenarios where users move between network types and need a stable, fast VPN connection.
Ease of management
User-Friendly: IPSec and IKEv2 are generally easier to manage and integrate into existing network infrastructures due to broad device support and straightforward setup.
Regulatory compliance
Ensure that the chosen VPN protocol meets any relevant regulatory and compliance standards. This is particularly important in sectors like healthcare and finance.
Your choice should align with your organization’s security standards, technical capacity, and specific use cases. Consult with IT security experts to determine which VPN protocol best fits your organization’s needs, providing the necessary security without compromising performance or usability.
How to set up an MPLS Layer 3 VPN?
Setting up a Layer 3 VPN involves several steps, focusing on configuring both the client and server components to ensure secure and efficient communication between network sites. Here’s a general outline of the process:
Choose the proper VPN Protocol
Select a Layer 3 VPN protocol that meets your security, performance, and compatibility needs. Common choices include IPSec, L2TP/IPSec, and OpenVPN.
Server configuration
Install the VPN Software: Install the necessary VPN software on the server depending on the chosen protocol.
Configure VPN Parameters: Set up encryption settings, authentication methods, and VPN tunnels. Define what traffic will be allowed through the VPN.
Set Routing Policies: Configure routing protocols to manage traffic between VPN endpoints. Depending on the network requirements, this may involve setting up BGP or OSPF.
Client configuration
Install VPN Client Software: Ensure the client device has the appropriate software installed to support the chosen VPN protocol.
Configure VPN Connection: Input the required server details, encryption settings, and credentials. This setup usually parallels the server settings to ensure compatibility.
Testing and troubleshooting
Test the Connection: Test the VPN connection for integrity and security after setting up both ends. Check if the data is appropriately encrypted and the sites are communicating securely.
Troubleshoot Any Issues: If there are connectivity or performance issues, troubleshoot by checking the VPN logs, verifying the encryption parameters, and ensuring that routing and firewall settings are correctly configured.
Maintenance and monitoring
Regular Updates: Keep the VPN software and hardware updated to protect against vulnerabilities.
Monitor VPN Performance: Regularly monitor VPN traffic, usage patterns, and performance to optimize the network and prevent potential issues.
Setting up a Layer 3 VPN can be complex and requires specialized knowledge, especially when dealing with advanced encryption and routing configurations. Consulting with or hiring network professionals is often beneficial if in-house expertise is lacking.
In conclusion, understanding Layer 3 VPN protocols is crucial for optimizing network performance, security, and scalability. Whether you want to implement MPLS, GRE, or IPsec protocols, each offers unique advantages tailored to specific network requirements. Stay informed and explore the diverse options available to ensure your network meets the demands of modern connectivity. Feel free to visit Proxy Rotating to explore more helpful information.
>>> See more:
Vpn gate public vpn relay servers
Vpn route based vs policy based
