What is Onion over VPN, and why is it ideal for safeguarding your online information? This article, Proxy Rotating, will answer all your questions, providing an in-depth look at this technology and how it operates. We’ll explore the unique benefits of Onion over VPN in enhancing network security and protecting personal privacy. Dive in to learn how Onion over VPN combines the power of the Tor network with VPN to create robust dual-layered security. Join us as we delve into the details and discover how this technology can help you browse the internet more securely and privately!
What is Onion Over VPN?
Onion Over VPN, also known as Tor over VPN, is a privacy solution that combines the anonymity and security of the Tor network with the encryption and security of a VPN. It involves connecting to a VPN server before accessing the Tor network, which adds privacy and security to your online activities.
How Does Onion Over VPN Work?
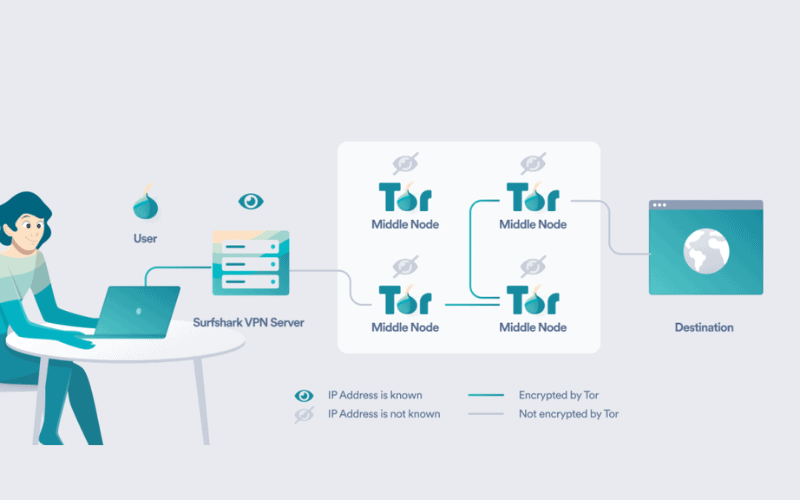
Onion Over VPN works by combining the privacy and security features of the Tor network with the encryption and anonymity provided by a VPN. Here is a detailed explanation of how Onion Over VPN operates:
- VPN Connection:
- Initially, you connect to a VPN server using a VPN app, which encrypts your internet traffic and changes your IP address, ensuring your online activities are secure and private.
- Tor Network Access:
- After establishing the VPN connection, you access the Tor network using the Tor browser. Your VPN connection is routed through multiple Tor servers, each encrypting your data, making it difficult to trace back to your original IP address.
- Data Encryption:
- As your connection travels through the Tor network, your data is encrypted multiple times, enhancing security and privacy. Each Tor server decrypts one layer of encryption before forwarding your traffic to the next server.
- Anonymity and Privacy:
- Onion Over VPN ensures that your IP address is hidden from the entry node of the Tor network, protecting your identity from potential monitoring within the Tor network. It also shields your online activities from third parties, including your internet service provider (ISP).
- Access to the Dark Web:
- This setup allows you to securely access the dark web, which is inaccessible through regular browsers. It provides an additional layer of privacy and security for browsing sensitive content.
- Increased Security:
- By encrypting your data multiple times and routing it through both the VPN and Tor network, Onion Over VPN offers enhanced security, making it challenging for malicious actors to intercept or track your online activities.
In summary, Onion Over VPN works by routing your connection through a VPN server before accessing the Tor network. It provides multiple layers of encryption and anonymity to safeguard your online privacy and security.
How to Set Up Onion over VPN
To set up Onion over VPN, follow these steps:
- Connect to your VPN: Use a VPN app like CyberGhost VPN to connect to a VPN server. This encrypts your internet traffic and hides your IP address.
- Download and Install Tor Browser: Download and install the Tor browser from the official Tor website. This browser is designed to protect your anonymity by encrypting your traffic and routing it through multiple nodes.
- Open the VPN App and Connect to a Server: Open the VPN app and connect to a VPN server. This ensures that your entire connection is encrypted and anonymous.
- Open the Tor Browser and Connect to the Onion Network: Open the Tor browser and connect to the Onion network. This encrypts your traffic multiple times and routes it through various nodes, making it difficult to trace back to your original IP address.
Tips and Precautions
- Choose a VPN That Supports Tor Traffic: To ensure seamless integration, ensure your VPN provider supports Tor traffic.
- Use a VPN with a Strict No-Logs Policy: Select a VPN with a strict no-logs policy to ensure your data is not logged or shared with authorities.
- Be Aware of Potential Drawbacks: Onion over VPN can be slow due to the additional encryption and routing through multiple nodes. Also, some VPN providers may have a reputation for selling user data or handing it over to authorities.
Onion over VPN is a powerful privacy solution that combines the anonymity and security of the Tor network with the encryption and security of a VPN. By following these steps and choosing a reputable VPN provider, you can enjoy enhanced privacy and security while browsing the internet.

Who should use Onion Over VPN?
Onion Over VPN benefits individuals who require an extra layer of privacy and security while using the internet. Specifically, the following groups can benefit from using Onion Over VPN:
- Journalists and Whistleblowers: Those handling sensitive information and prone to surveillance can benefit from the heightened privacy and anonymity provided by Onion Over VPN. It allows them to communicate, research, and publish content with increased confidence.
- Human Rights Activists and Dissidents: Individuals advocating for political or social causes in repressive regimes can communicate and access information securely using Onion Over VPN to remain anonymous and protect their safety.
- Researchers and Data Handlers: Academic researchers and individuals working with sensitive data can maintain confidentiality and anonymity while accessing resources and communicating with colleagues without compromising research objectives.
- Citizens and Travelers in Restrictive Countries: Those living in countries with strict censorship or surveillance measures can use Onion Over VPN to bypass restrictions and access the internet freely and securely.
- Privacy Advocates: Individuals who prioritize privacy and seek to safeguard their data from surveillance, advertisers, and data brokers can benefit from Onion Over VPN’s enhanced privacy and security.
In summary, Onion Over VPN is ideal for individuals who require complete anonymity, enhanced privacy, and protection from government censorship and surveillance while using the internet.
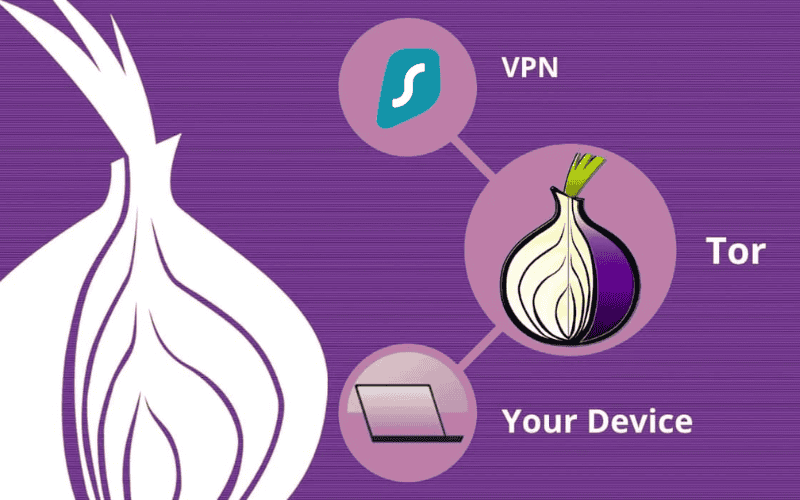
Why use Onion over VPN? Pros and cons?
Onion over VPN is a privacy solution that combines the anonymity and security of the Tor network with the encryption and security of a VPN. Here are the key points about why to use Onion over VPN and its pros and cons:
Why Use Onion Over VPN?
- Enhanced Privacy: Onion over VPN adds an extra layer of encryption and anonymity to your online activities, making it difficult for anyone to trace your activities back to you.
- Protection from Surveillance: Onion over VPN helps protect you from government surveillance and censorship by hiding your IP address and encrypting your data.
- Protection from Malicious Activity: Onion over VPN prevents malicious actors from intercepting and understanding your data, even if they are on the same network.
- Protection from Traffic Correlation Attacks: Onion over VPN reduces the likelihood of attackers correlating traffic entering and exiting the Tor network to de-anonymize users.
- Protection from ISP Tracking: Onion over VPN hides your ISP from seeing that you are using Tor, reducing the risk of disconnection or reporting.
Pros and Cons of Onion Over VPN
Pros:
- Enhanced Privacy: Onion over VPN provides enhanced privacy by hiding your IP address and encrypting your data.
- Protection from Surveillance: Onion over VPN helps protect you from government surveillance and censorship.
- Protection from Malicious Activity: Onion over VPN prevents malicious actors from intercepting and understanding your data.
- Protection from Traffic Correlation Attacks: Onion over VPN reduces the likelihood of attackers correlating traffic entering and exiting the Tor network.
Cons:
- Slow Connection Speeds: Onion over VPN can be slow due to the additional encryption and routing through multiple nodes.
- Potential for Compromised Exit Nodes: The Tor network is run by volunteers, so there is a risk of compromised exit nodes that could expose your activities.
- Potential for VPN Provider Analysis: Your VPN provider could analyze your traffic before it is encrypted by the Tor network, which could compromise your privacy.
Onion over VPN is a powerful privacy solution that combines the anonymity and security of the Tor network with the encryption and security of a VPN. While it offers enhanced privacy and security, it also has some drawbacks. To ensure your safety while using Onion over VPN, it is essential to choose a reputable VPN provider with a no-logs policy and a kill switch feature.
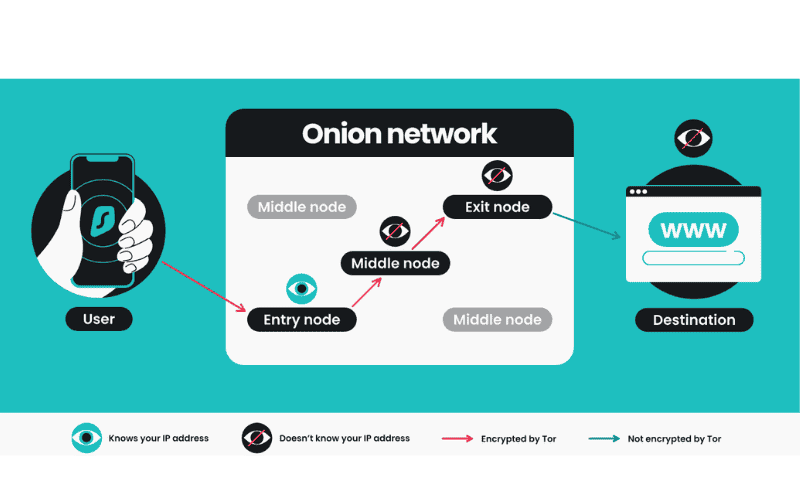
When to Use Onion Over VPN?
- Government Censorship and Surveillance: Onion over VPN is particularly beneficial for individuals who must avoid government censorship and surveillance. Using a VPN before accessing the Tor network ensures that your ISP cannot detect your Tor usage and that your IP address remains hidden throughout the process.
- Journalists and Activists: Journalists, bloggers, and activists who must maintain complete anonymity while accessing sensitive information or communicating with sources can benefit from Onion over VPN. This setup helps protect their identities and activities from government surveillance and censorship.
- Dark Web Access: Onion over VPN helps access the dark web, which is inaccessible through regular browsers. This setup provides enhanced security and anonymity for users accessing sensitive or illegal content.
- High-Risk Activities: Individuals engaging in high-risk activities, such as whistleblowing or sharing sensitive information, can benefit from the added security and anonymity provided by Onion over VPN.
- Public Wi-Fi and Streaming: While not necessary for casual users, Onion over VPN can benefit those who frequently use public Wi-Fi or need to access geo-restricted content. It provides an extra layer of security and anonymity for these activities.
Onion over VPN is a powerful privacy solution that combines the anonymity and security of the Tor network with the encryption and security of a VPN. Choosing a reputable VPN provider with a no-logs policy and a kill switch feature is essential to ensure your safety while using Onion over VPN.
When don’t you need Onion Over VPN?
You don’t need Onion Over VPN in the following situations:
- Casual Internet Browsing: A VPN protects your privacy and security for general internet use. Onion Over VPN is not necessary for casual browsing, social media, or accessing identity-linked websites.
- Speed-Critical Activities: Onion Over VPN can significantly reduce internet speeds due to the multiple encryption and routing processes involved. If speed is a primary concern, using a VPN alone or over Tor might be a better option.
- Accessing Identity-Linked Websites: Onion Over VPN is unnecessary for accessing websites that require your real identity, such as social media or online banking. A VPN alone can protect your privacy and security in these situations.
- Simple To Use: If you only need to access the Tor network for specific purposes, using Tor alone without a VPN might be sufficient. However, Onion Over VPN is recommended to protect your IP address and information before entering the Tor network.
- Unreliable VPNs: Not all VPNs are suitable for Onion Over VPN due to security and performance issues. If your VPN provider lacks necessary security features or is unreliable, choosing a different VPN that supports Onion Over VPN is better.
In summary, Onion Over VPN is not necessary for casual internet use, speed-critical activities, accessing identity-linked websites, simple Tor use, or unreliable VPNs. It is primarily beneficial for individuals who must maintain complete anonymity while using the internet, such as journalists, activists, or countries with strict censorship and surveillance.
The difference between Onion over VPN and Regular VPN
The differences between Onion over VPN and a regular VPN lie primarily in the layers of privacy, the routing process, and the intended use cases. Here’s a detailed comparison to help illustrate these distinctions:
| Characteristics | Regular VPN | Onion over VPN |
| Privacy and Anonymity Levels | A VPN encrypts your internet traffic and routes it through a chosen or assigned server. This changes your IP address and secures your data from external observation, such as ISPs or hackers. However, the VPN provider can still see your traffic and, if not properly secured, could potentially access your data. | This service adds an extra layer of privacy by routing your VPN-encrypted traffic through the Tor network. With this setup, your traffic passes through multiple Tor nodes, each adding a new layer of encryption, making it extremely difficult for anyone to trace the activity back to you. Even if a party could observe your connection, they would only see it coming from the Tor exit node, not the VPN server or your original IP. |
| Routing Process | Traffic is directly routed through a VPN server. The route is straightforward and usually optimized for speed and reliability, depending on the VPN provider’s infrastructure. | After passing through the VPN server, traffic is sent through the Tor network, which involves multiple randomly selected nodes. Each node decrypts a layer of encryption to know where to send the data next but cannot trace the entire path or the source. |
| Speed and Performance | VPNs generally provide faster speeds as they directly route through one or more dedicated servers. They are often optimized for speed and can handle high-bandwidth activities like streaming gaming or large downloads. | The routing through multiple Tor nodes, each adding and removing layers of encryption, significantly slows down the connection. This setup is unsuitable for high-bandwidth activities and better suited for tasks where privacy is more important than speed. |
| Use Cases | Ideal for everyday internet usage, such as browsing, streaming, or downloading. It’s also widely used for securing connections on public Wi-Fi and bypassing geographical content restrictions. | It is best suited for users requiring the highest level of anonymity and security, such as journalists working in sensitive political contexts, activists, or anyone needing to access the internet under strict surveillance or censorship without leaving a trace. |
| Security Risks | Risks are primarily dependent on the trustworthiness and protocol security of the VPN provider. Users must trust that the VPN does not log or misuse their data. | Adds protection against rogue Tor nodes. Encrypting traffic before it enters the Tor network protects potentially sensitive data even if it passes through a compromised Tor exit node. The VPN layer obscures entry into the Tor network, offering protection against targeted surveillance that might occur if one’s use of Tor were detected. |
In summary, while Onion over VPN and regular VPN services provide privacy and security, Onion over VPN offers a superior level of anonymity at the cost of speed and performance. It is precious in extreme privacy scenarios where users must avoid tracking or interception at all costs.
Benefits of Onion over VPN
Using Onion over VPN provides significant benefits, especially for those who prioritize high levels of privacy and security when online. Here’s a breakdown of the essential advantages:
Optimal online security and privacy
- Hiding your IP address and actual location: Onion over VPN effectively masks your real IP address and geographic location. This prevents websites, ISPs, and malicious actors from tracking your real-world identity or location, providing an essential layer of privacy.
- Multiple Encryptions of Traffic: Traffic passing through Onion over VPN is encrypted numerous times—first by the VPN and then by each node within the Tor network. This layered encryption ensures that decoding it would be extremely challenging even if the traffic is intercepted.
- Protection from Surveillance and Tracking: With its robust encryption and routing techniques, Onion over VPN makes it virtually impossible for government agencies or network administrators to monitor your online activities. This is crucial for users in regions with strict censorship or surveillance.
Access to blocked content
- Bypassing Firewalls and Internet Censorship: Onion over VPN can navigate through strict firewalls and bypass government-imposed censorship, granting access to the free internet.
- Access to Websites Blocked in Your Region: This setup allows users to circumvent geo-restrictions, providing access to content and websites that are otherwise unavailable in their countries due to regional restrictions or bans.
Protection from online threats
- Protection from Malware, Cyber-attacks, and Hackers: The encryption and anonymity provided by Onion over VPN protect users from various online threats, including malware that might be encountered on less secure websites.
- Keeping Personal Data and Sensitive Information Safe: For anyone transmitting sensitive information—personal data, financial details, or confidential communications—Onion over VPN ensures that this data remains secure and private, mitigating the risk of identity theft and data breaches.
Some VPNs support Onion over VPN.
- NordVPN: Known for its robust security features, NordVPN offers Onion over VPN as one of its advanced features, ensuring enhanced privacy and anonymity.
- ExpressVPN: A popular choice among users, ExpressVPN supports Onion over VPN, allowing you to combine the benefits of VPN encryption with the anonymity of the Tor network.
- CyberGhost VPN: CyberGhost VPN provides Onion over VPN functionality, offering users an extra layer of privacy and security when browsing online.
- Surfshark: Surfshark is another VPN provider that supports Onion over VPN, providing users with enhanced privacy protection and unrestricted access to the internet.
- VyprVPN: With its proprietary Chameleon protocol, VyprVPN supports Onion over VPN, offering robust encryption and bypassing restrictions to ensure a secure and open internet experience.
- ProtonVPN: ProtonVPN offers Onion over VPN as part of its security-focused features, allowing users to combine the benefits of both VPN and Tor for maximum privacy and security.
- Private Internet Access (PIA): PIA supports Onion over VPN, providing users additional layers of encryption and anonymity to protect their online activities.
When choosing a VPN that supports Onion over VPN, consider factors such as server locations, connection speeds, customer support, and pricing to find the best option that meets your specific needs for online privacy and security.

FAQ about Onion Over a VPN
Is Onion over a VPN Safe?
Onion over VPN is generally safe to use, but there are risks associated with the Tor network, such as potential vulnerabilities in exit nodes. However, when combined with a secure VPN service, Onion over VPN can enhance privacy and security by adding an extra layer of encryption and anonymity to your online activities.
Is Onion over a VPN Better than a Double VPN?
Onion over VPN and Double VPN serve different purposes. Onion over VPN involves connecting to a VPN server before accessing the Tor network, adding an extra layer of privacy and encryption. On the other hand, Double VPN routes your connection through two VPN servers for enhanced security. The choice between the two depends on your specific privacy and security needs.
What Is Onion over a VPN Used For?
Onion over VPN combines the privacy and anonymity features of the Tor network with the encryption and security of a VPN. It provides users with enhanced privacy, security, and anonymity online, making it a popular choice for those seeking to protect their online activities from surveillance and tracking.
Is a VPN Safe for Online Banking?
Using a VPN for online banking can enhance security by encrypting your internet connection and protecting your data from potential threats. However, choosing a reputable and secure VPN service is essential to ensure the safety of your online banking activities. Additionally, make sure to connect to a server in your own country to avoid potential issues with accessing your banking services
Proxy Rotating has provided information to answer the question, “What is Onion over VPN?” Hopefully, this article will help you better understand Onion over VPN and its benefits. Visit the Proxy Rotating website, http://proxyrotating.com, to explore more knowledge!
>>> See more:
