Virtual Private Networks (VPNs) are crucial in improving online privacy and security. By creating a secure and encrypted connection over the Internet, VPNs protect your data from eavesdroppers, hackers, and even your Internet Service Provider (ISP). This level of security is crucial when using public wi-fi networks or accessing sensitive information online. VPNs function by routing your Internet traffic through remote servers, hiding your IP address, and encrypting data transmissions, thus making your online activities virtually untraceable. With VPN Can I be tracked? To learn more about the security features of VPNs, please follow the upcoming article by Proxy Rotating.
Can you be tracked with a VPN?
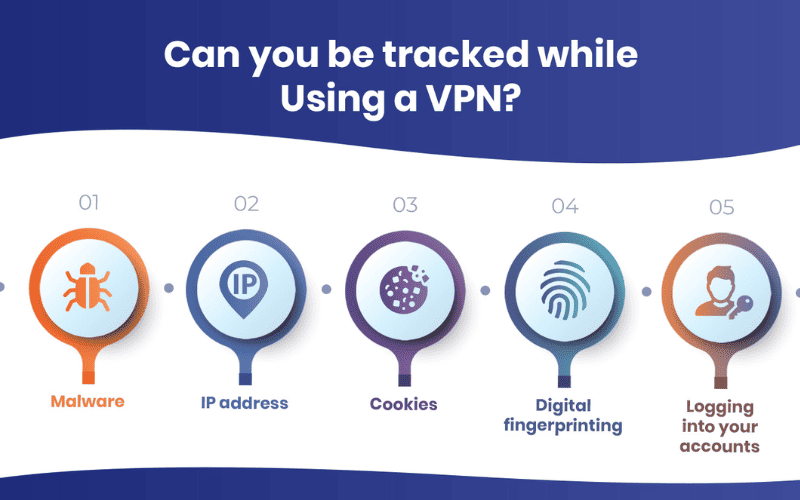
Using a VPN enhances your online privacy and security by encrypting your internet traffic and hiding your IP address, but there are better solutions than this. You can still be tracked when using a VPN if you don’t take additional precautions. Here are some of the ways you might still be tracked even when using a VPN:
Malware
If your device is infected with malware or spyware, a VPN won’t protect you from being tracked. Malware can log your keystrokes, capture your screen, or steal files and cookies directly from your device.
Cookies
Cookies can track your browsing activity across sites. Even when using a VPN, if you log into a website, that website can use cookies to track your activities on their site and recognize you when you return, even from a different IP address.
WebRTC Leaks
WebRTC (Web Real-Time Communication) is a protocol that can leak your real IP address even while using a VPN. Browsers use WebRTC for voice, video chat, and peer-to-peer file sharing directly in the browser. Disabling WebRTC or using browser extensions that block WebRTC can help prevent these leaks.
DNS Leaks
DNS requests translate domain names into IP addresses. Sometimes, even when connected to a VPN, the device might use the default DNS server provided by the ISP instead of the VPN’s DNS server, leading to DNS leaks. This can expose your browsing data to your ISP or a DNS service. Good VPN providers offer DNS leak protection to ensure all DNS requests are routed through the VPN.
Browser fingerprinting
This technique uses your browser’s unique configuration (such as browser version, screen resolution, installed fonts, and plugins) to identify and track you. Browser fingerprinting can track you across different sessions, even using a VPN. Using browsers focusing on privacy or configuring your browser to reduce uniqueness can help mitigate this.
Who can track you online?
Various entities can conduct online tracking, each with different capabilities and purposes. Here’s a breakdown of who might be tracking your online activities and how:
- Internet service providers (ISPs): Your ISP can see your internet activity, including the websites you visit and the data you send and receive. This visibility is because all your internet traffic passes through their infrastructure. ISPs may track your activities for data optimization, marketing, and legal compliance.
- Websites and Online Services: Websites you visit can track your behavior on their sites through cookies, web beacons, and other tracking technologies. They collect data on how long you stay on pages, what you click on, and other interactions to improve user experience and deliver targeted advertisements.
- Advertisers and third-party trackers: Advertisers often use third-party cookies and tracking scripts embedded in multiple websites to track their online activities. This allows them to profile your interests and behavior to serve more relevant ads.
- Social media platforms: Social media companies track your interactions within their platforms—what you like, share, or post. This tracking can extend to other sites if they feature social media plugins (like “Like” buttons), which can send information back to the social media platform even if you don’t interact with them.
- Search engines: When you use a search engine, it collects data about your search queries, sometimes linking them to your account if logged in. This data can be used to refine your future search results and for targeted advertising.
- Governments and law enforcement: Under certain conditions, government agencies and law enforcement might track online activities as part of investigations or for national security purposes. They may require ISPs or tech companies to provide user data.
- Hackers and cybercriminals: These actors may use malicious software, phishing attacks, or exploit security vulnerabilities to track your activities and steal personal information. Their motivations can range from financial gain to identity theft.
- Mobile apps: Many apps request permission to access your location, device information, and other personal data. Some of this data can be used to track your activities, improve services, and target advertising.
Each of these entities has different tracking methods and motivations. Protecting yourself online involves understanding these tracking technologies and taking steps like using VPNs, enabling privacy settings, avoiding suspicious links, and regularly clearing cookies.
How to be untraceable online?
Being completely untraceable online is extremely difficult, but you can use several strategies to increase your privacy and reduce your digital footprint significantly. Here are some of the most effective methods:
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic and routes it through a server in a location of your choice, masking your IP address and preventing your Internet Service Provider (ISP) and others from seeing your internet activity.
Use secure browsers: Opt for browsers that prioritize privacy, such as Tor. This anonymizes your browsing by routing your internet traffic through multiple nodes, making it difficult to trace activity back to you. Privacy-focused browsers like Brave or Firefox (with privacy settings adjusted) can also help. - Enable privacy settings: To minimize data sharing, adjust the privacy settings on your browser and websites. Use browser extensions like Privacy Badger or uBlock Origin to block trackers.
- Use encrypted communication tools: Opt for services that offer end-to-end encryption for messaging and calling, such as Signal or Telegram (with a secret chat feature). This encryption ensures that only the sender and receiver can read messages.
- Use secure and private email services: ProtonMail and Tutanota offer encrypted email solutions that are less likely to track your activity or scan your emails for advertising purposes.
- Avoid social media sharing: Be cautious about what you share on social media. The more information you share, the easier it is to track your activities and interests.
- Use anonymous payment methods: To avoid leaving a digital trail associated with credit/debit cards or PayPal, use cash or cryptocurrencies for transactions.
- Clear cookies and cache regularly: Cookies and cache can store information about your browsing habits and preferences. Clearing them regularly reduces the data that websites can collect about you.
- Use fake information when possible: For services that don’t require your real identity, consider using pseudonyms and avoiding providing accurate details such as your full name, address, and birthdate.
- Disable Ad-tracking: Look for options to disable ad tracking on devices and online services. This reduces the amount of data advertisers collect about you.
- Secure your devices: Use strong passwords, enable two-factor authentication, and update your software to protect against unauthorized access and exploits.
Employing these strategies can significantly increase your anonymity and privacy online. However, remember that no method is foolproof, and maintaining privacy online requires consistent effort and vigilance.
Tips for choosing a secure VPN
Choosing a secure and reliable VPN is crucial for ensuring online privacy and security. Here are some tips to help you select a VPN that meets high standards of security and trustworthiness:
- Reputation and reviews: Start by researching the reputation of various VPN providers. Look for reviews from reliable tech websites and check user reviews on forums and other online platforms to gauge other users’ experience and trust in the VPN.
- No-logs policy: Opt for a VPN provider with a strict no-logs policy, meaning they do not keep records of your internet activities. This policy should be clearly stated and verified through independent audits.
- Strong encryption: Ensure the VPN uses up-to-date encryption standards such as AES-256 to protect your data. This is the same level of encryption used by governments and security experts worldwide.
- Security protocols: Look for VPNs that offer a range of secure VPN protocols. OpenVPN and WireGuard are currently considered some of the most secure and reliable options.
- Kill switch: A kill switch is a critical security feature that stops all internet traffic if the VPN connection drops unexpectedly. This ensures that your data is not transmitted over an unsecured connection.
- DNSbleak protection: The VPN should provide DNS leak protection to ensure that all DNS requests are routed through the VPN tunnel, preventing your ISP from seeing your browsing activities.
- Jurisdiction: Consider where the VPN service is based and the country’s privacy laws. Countries outside the “14 Eyes” surveillance alliance (a group known for extensive cooperation in data surveillance and sharing) are often preferred for stricter privacy protections.
- Transparency: Check if the company is transparent about its operations, policies, and technology. Some VPNs undergo independent audits to verify their security and privacy claims and publicly share the results.
- Server security: The VPN should offer a wide range of server locations and ensure their servers are secure. Some VPNs use RAM-only servers, which means all information on the server is wiped every time it is rebooted, enhancing data security.
- Performance: While not directly related to security, a VPN’s performance affects your overall experience. Look for a VPN that provides fast speeds and reliable connections to ensure it can handle activities like streaming, gaming, or large downloads.
- Customer support: Good customer support is essential. Ensure the VPN provider offers competent, responsive, and accessible customer service.
- Price and value: Compare pricing among reputable providers to ensure you get good investment value. Be wary of free VPN services; they might compromise your security by logging your data or displaying ads.
When selecting a VPN, it’s often wise to test it through a free trial or a money-back guarantee period to ensure it meets your needs and expectations in terms of both security and performance.
Factors affecting the traceability when using a VPN
VPN significantly enhances online privacy and security by encrypting your internet connection and masking your IP address. However, the question arises, “With VPN can I be tracked?” Several factors can affect the traceability of your online activities, even when you’re using a VPN. Understanding these factors can help you minimize your digital footprint:
VPN provider’s logging policy
A VPN provider’s logging practices are crucial. Providers that keep logs of your online activities, connection times, and IP addresses could compromise your privacy if authorities request or leak these logs.
IP/DNS leaks
VPN connections can sometimes fail, leading to IP or DNS leaks where your actual IP address or the websites you visit leak out of the VPN tunnel. This can happen due to software vulnerabilities, incorrect configurations, or network issues.
WebRTC leaks
WebRTC (Web Real-Time Communication) is a protocol that enables direct browser-to-browser communication. However, it can also inadvertently expose your IP address, even when using a VPN. Disabling WebRTC in your browser settings or using a VPN that blocks WebRTC can mitigate this risk.
Payment Information
The method you use to pay for the VPN service can leave a trace back to you. Traditional payment methods (credit cards, PayPal) are less private than anonymous payment options like cryptocurrencies or gift cards.
Use of cookies and tracking scripts
Websites use cookies and other tracking mechanisms to follow users across the web. A VPN does not prevent these trackers from collecting information on your browsing habits, which can be used to identify you.
Malware on your device
If your device is infected with malware or spyware, it could bypass your VPN protection, track your activities, or steal sensitive information directly from your device.
Browser fingerprinting
Websites can use browser fingerprinting techniques to collect information about your device and browser settings, creating a unique profile that can track you across the web, independently of your IP address.
Encryption strength and protocols
The strength of the encryption and the security of the protocols used by the VPN can affect how easily your data can be intercepted and decrypted by third parties.
Global surveillance alliances
Depending on the jurisdiction of your VPN provider, it may be subject to laws that compel it to collect or hand over data on its users to government agencies, as seen with the Five Eyes, Nine Eyes, and Fourteen Eyes alliances.

Scenarios in which you might be tracked while using a VPN
Specific scenarios can lead to tracking or compromise privacy even when using a VPN. Understanding these scenarios can help you take additional precautions:
The VPN provider keeps logs
If your VPN provider logs your browsing history, connection times, IP addresses, or other data, authorities could access these logs through legal demands or inadvertently expose them through data breaches. This raises the question, “with VPN can I be tracked?”
IP or DNS leaks
Software flaws, misconfigurations, or specific network conditions can cause your actual IP address or DNS requests to leak outside the VPN tunnel, revealing your exact location and the sites you visit.
Payment information
Signing up for a VPN service with identifiable payment methods (like credit cards or PayPal) can be traced back to you, potentially compromising your anonymity.
Use of cookies and browser fingerprinting
Cookies can track your online activities across different sessions and sites, while browser fingerprinting can identify you based on your device and browser characteristics, regardless of your IP address.
WebRTC leaks
WebRTC enables peer-to-peer communication within web browsers but can also disclose your IP address, even when using a VPN, if not properly blocked or disabled in browser settings.
Targeted malware or spyware
If your device is infected with malware or spyware, it could directly monitor your activities and steal sensitive information, bypassing VPN protections.
Using insecure or compromised VPN protocols
Outdated or insecure VPN protocols can be vulnerable to decryption or other attacks, potentially exposing your data.
Global surveillance and compelled data sharing
Depending on the jurisdiction, VPN providers might be legally compelled to collect and hand user data to government agencies as part of surveillance programs.
Active network monitoring or attacks
Sophisticated attackers or agencies with the capability to monitor network traffic at a large scale might employ advanced techniques to infer activity or target specific users. However, decrypting VPN-protected traffic directly is highly challenging. This scenario underscores the concern: can tracking occur even with a VPN?

How to secure your data when using a VPN?
Securing your data while using a VPN involves more than just turning on the VPN itself. It requires a combination of good digital hygiene practices, careful selection of a VPN provider, and additional security tools and behaviors. Here are some key strategies to enhance your data security when using a VPN:
Choose a reputable VPN provider
Opt for a VPN provider known for its strong commitment to privacy and security. Look for features such as AES-256-bit encryption, a strict no-logs policy, and a kill switch.
Research the provider’s jurisdiction and policies to ensure they align with your privacy needs.
Keep the VPN software updated.
Regularly update your VPN application to protect against known vulnerabilities. Software updates often include patches for security issues that could compromise your data.
Be cautious about public wi-fi.
Exercise caution when using a VPN to connect to public wi-fi networks. Refrain from logging into sensitive accounts or performing financial operations unless essential.
Use strong passwords and authentication.
Implement robust, unique passwords for all your accounts, especially your VPN account. Consider adopting a password manager for secure password management. Two-factor authentication (2FA) should be activated wherever possible to add an extra security layer.
Manage cookies and online tracking.
Regularly clear your cookies or use incognito/private browsing modes to minimize tracking.
Use browser extensions that block trackers and ads to reduce your online footprint.
Consider additional privacy tools.
In addition to a VPN, consider using privacy-focused browsers, search engines, and other tools like the Tor browser for activities requiring higher levels of anonymity.
Be mindful of permissions and sharing.
Carefully review the permissions requested by apps and services. Limit the sharing of location and personal information only to trusted applications and when necessary.
By following these practices, you can significantly enhance the security of your data when using a VPN, protecting yourself against various online threats and ensuring a safer internet experience.

What is the best VPN to prevent tracking?
When evaluating the safety of VPNs, it’s essential to consider the security features, encryption protocols, and privacy policies they offer. While no single type of VPN can be declared the absolute safest, as security also depends on how they’re implemented and used, certain VPN types and features stand out for providing higher levels of security:
OpenVPN
Security: Widely regarded as the gold standard for VPN protocols, OpenVPN offers robust protection and is highly configurable to suit different encryption needs. It supports AES-256-bit encryption, which is military-grade security.
Compatibility: Works on most devices and platforms, including routers.
Open Source: The open-source nature allows for regular auditing by the community, ensuring vulnerabilities are identified and patched.
WireGuard®
Security: A newer protocol is known for its lean and simple codebase, which makes it easier to audit and less prone to security vulnerabilities. It offers strong encryption and aims to outperform OpenVPN and IPSec in speed and reliability.
Performance: Designed for better performance in terms of speed and connection stability.
Development Stage: While promising, it’s relatively new and has no shorter track record than OpenVPN. However, its simplicity and efficiency make it a strong contender.
IKEv2/IPSec
It provides robust security and is particularly well-suited for mobile devices due to its support for MOBILE, which allows it to smoothly handle network changes (like switchiWi-Fiom wi-fi to mobile data).
Speed and Stability: It is known for its fast connection speeds and stability, making it ideal for use on smartphones and tablets.
Compatibility: Supported by many platforms but less widely than OpenVPN.
FAQs:
Can police track VPNs?
Yes, with the proper legal authority, such as warrants, police can request information from VPN providers. Depending on the provider’s logging policies and jurisdiction, they may need help to provide helpful information.
Can employers track VPNs?
Yes, if you’re using a VPN provided by your employer, they can track your VPN usage logs, including when you connect and disconnect and possibly which services you access through their network.
Can you be tracked with a free VPN?
Yes, many free VPNs do not follow strict no-logs policies and may collect and possibly sell your browsing data to third parties for marketing or other purposes.
Can Google track you with a VPN?
Yes, if you are logged into your Google account, Google can still track your activities across its services, such as Google Search, YouTube, and Gmail, regardless of the VPN.
Can you be tracked if your VPN connection drops?
If the VPN connection drops and the VPN does not have a kill switch, your internet activities may be exposed to your ISP or any network monitoring until the VPN connection is restored.
Thus, the article above answered, “With VPN can I be tracked?” In addition, Proxy Rotating has supplied valuable information regarding the safety level of VPNs. This article lets readers learn more about VPNs and choose their best VPN type. To explore more related information, please visit the website https://proxyrotating.com/ right now.
>>> See more:
With vpn connected no internet
